Here’s a no-cost way to complete gen eds. Get details
Online Bachelor of Science in Information Technology Cybersecurity
PROGRAM AT A GLANCE
40 bachelor's courses
11 weeks long
$ 1555
Cost per course
Flexible learning
Online and in-person programs at select campuses, subject to availability
Why earn a cybersecurity degree from Strayer?
Who knows where the cyber threat will come from, and who will suffer from an attack? If you want to be one of the good guys guarding important data, consider earning a BS in Information Technology, Cybersecurity from Strayer University. You’ll build skills in conducting digital forensics, learn how to help protect data and networks, and defend against a digital onslaught, whatever its source.
Defend networks from cybersecurity threats
Learn how to protect the security of networks, data and other assets with an online BSIT in Cybersecurity from Strayer. You’ll build your knowledge of network defense and countermeasures, explore different types of hacking – and its ethical applications – and learn how to analyze information security to help defend people and organizations against cybercrime.
Skills you’ll learn in a Strayer BSIT, Cybersecurity concentration
A Strayer degree can help prepare you for career opportunities in cybersecurity while offering support, flexible learning options and career planning every step of the way.
- Learn how to maintain the security of networks in a range of environments.
- Study different types of hacking (both ethical and unethical).
- Perform penetration tests and information security analysis.
- Study offensive network security, ethical hacking, network defense and their countermeasures.
Earn your degree from an accredited university
Strayer University is an accredited institution and a member of the Middle States Commission on Higher Education (MSCHE or the Commission) www.msche.org. Strayer University’s accreditation status is Accreditation Reaffirmed. The Commission’s most recent action on the institution’s accreditation status on June 22, 2017 was to reaffirm accreditation. MSCHE is recognized by the U.S. Secretary of Education to conduct accreditation and pre-accreditation (candidate status) activities for institutions of higher education including distance, correspondence education, and direct assessment programs offered at those institutions. The Commission’s geographic area of accrediting activities is throughout the United States.

Bachelor of Science in Information Technology in Cybersecurity cost breakdown
- 40 courses, $1555 per course
- $65 technology fee each term
- $150 one-time degree conferral fee
- $100 resource kit per course
Estimate the cost of your degree
How much does a Bachelor of Science in Information Technology in Cybersecurity cost?
Estimate the cost of your degree
How much does a Bachelor of Science in Information Technology in Cybersecurity cost?
Expected Graduation
...
Approximate Total
...
*Student is required to take two courses per quarter during disbursement period
PREPARING YOUR RESULTS
Time commitment
Calculate the approximate time commitment of your degree.
| Course load | ... courses/term |
| Classroom time | ... hours/week |
| Terms per year | ... terms |
| Terms to graduation | ... terms |
Cost analysis
Calculate the approximate cost of your degree
| Tuition | ... |
| Books | ... |
| Fees | ... |
| No-cost gen ed | $0 |
| Transfer credits | ... |
| Transfer Credit Scholarship | $0 |
| $4K scholarship | $0 |
| Strayer Learn and Earn Scholarship | $0 |
| Approximate total | ... |
Opportunities to save on tuition
Employer Tuition Assistance
More than 500 organizations invest in their employees by partnering with Strayer University to offer access to discounted education programs.
The Strayer Learn and Earn Scholarship
For every three courses you pass, earn one on us, tuition-free, to be redeemed at the end of your program with the Strayer Earn and Learn Scholarship. Eligibility rules and restrictions apply. Connect with us for details.
Save up to $15,250 on your bachelor’s degree
As a Strayer student, you have access to no-cost gen ed courses through our affiliate, Sophia. Take up to two online Sophia courses at a time and transfer eligible courses towards your undergraduate degree.
*Savings assumes transferring 10 courses taken at Sophia. Eligibility rules apply. Connect with us for details.
Explore courses in Strayer’s Bachelor of Science in Information Technology, Cybersecurity
Digital crime is on the rise – are you ready to fight it? Discover how to secure an organization’s data and operations against cybercriminals. You’ll learn how to install, configure and maintain the Windows® server environment. Through hands-on labs, you’ll gain a practical understanding of tactics and tools used by hackers and how to defend critical infrastructure against them.
Cybersecurity concentration courses
CIS 332 Network Server Administration I
SEC 420 Perimeter Defense Techniques
SEC 435 Network Penetration Testing
SEC 340 Computer Forensic Technology
Complete your degree from where you live, on your time, in a flexible, 100% online program. Using our online portal, you’ll be able to:
- Access lectures and coursework
- Complete assignments and exams
- Communicate with professors and classmates
- Access student resources and support
From day one, you’ll have a team of advisors and coaches to help you balance college, work and your personal life. Tap into support resources online or at a campus near you.
You’ll have access to:
- Admissions and enrollment support
- One-on-one academic coaches
- Financial guidance and potential cost savings
- Career planning services
Strayer has many campuses where you can connect with your peers, chat with student coaches, access support resources and attend in-person hybrid classes (at select campuses only).
The faculty at Strayer University bring years of real-world industry experience to the classroom, offering valuable insight and practical knowledge. They are committed to supporting your professional goals and are responsive to questions and concerns through the virtual courseroom.
What can you do with a BS in IT, Cybersecurity degree?
Your education can help you pursue your professional and personal goals. While Strayer cannot guarantee that a graduate will secure any specific career outcome, such as a job title, promotion or salary increase, we encourage you to explore the potential impact you can have in the cybersecurity field.
Versatile skills for your future
The cybersecurity concentration can provide the skills to help you secure an organization’s data and operations against cybersecurity concerns.
- Audit network and security systems to reveal potential issues.
- Develop strategies to help clients respond to and recover from security breaches.
- Identify network intruders by analyzing log files and monitoring network traffic for suspicious activity.
- Implement security measures to help safeguard data and information systems.
- Keep digital media compliant with legal policies and procedures.
- Measure security controls and determine their effectiveness, using key performance indicators.
- Modify computer security files and manage individual access requests.
- Monitor networks for data breaches, phishing and other security threats.
- Prepare plans that protect computer files against unauthorized access, modification, destruction or disclosure.
- Regulate access to the files on your network and monitor how people interact with them, to keep data from falling into the wrong hands.
- Secure data transmissions and filter out unwanted intrusions, using encryption and firewall systems.
- Stay on top of the latest computer virus news to better time your security updates.
- Take a proactive and reactive approach to supporting cybersecurity initiatives.
84
of Strayer bachelor’s alumni agree that their Strayer degree gave them the confidence to advance their career.
Strayer Alumni Survey, 2023
Apply for your Cybersecurity degree today
An admissions officer can help you choose the right program, register for classes, transfer credits and find cost-savings opportunities.
Here’s what you’ll need to get started:
Spring classes start on April 6
Learn more about Strayer University’s admissions process.
Transferring to Strayer from another university?
Your bachelor’s degree from Strayer could be 70% complete when you transfer up to 28 classes.
Strayer welcomes international students
Strayer University is proud to have hosted more than 4,000 international students from over 110 countries. Earn your degree in the U.S. or completely online in your home country – it’s your choice.

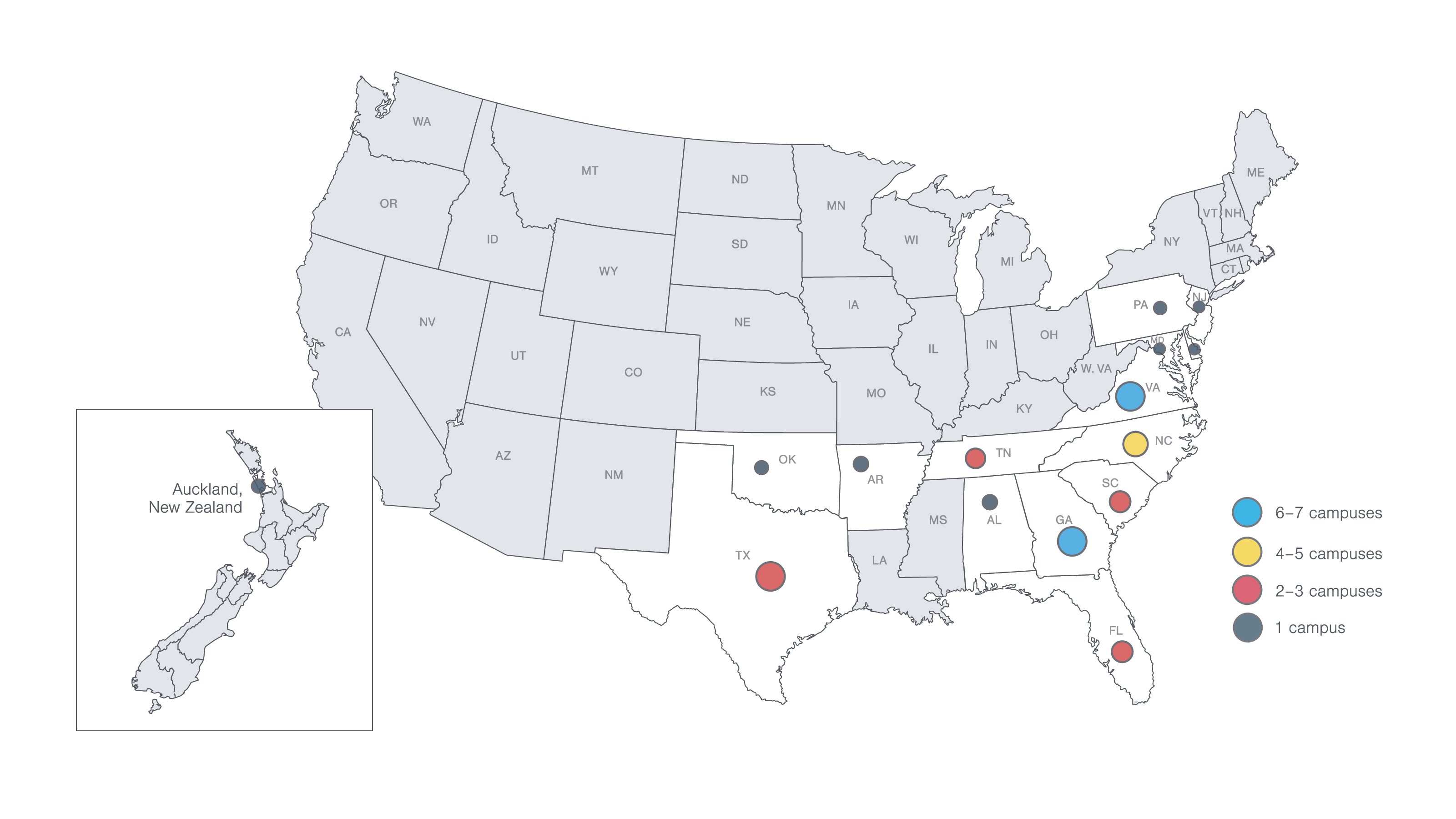
Campus locations
Come to a campus near you for guidance and support. You’ll have access to helpful resources, a supportive community and plenty of spaces to learn and grow.
Ready to take the next step?
Your admissions officer is here to guide you through every step of the process, from completing your application to choosing your concentration.