Master of Science in Information Systems (MSIS) Computer Security Management
PROGRAM AT A GLANCE
12 master's courses
11 weeks long
$ 2540
Cost per course
Flexible learning
Online and in-person programs at select campuses, subject to availability
Why earn a degree in computer security management from Strayer?
Earning an MS in Information Systems with a computer security management concentration from Strayer University will introduce you to the latest network encryption and data monitoring techniques. This online program can help prepare you to protect computer network systems from malware, intruders and more.
Safeguard network systems and protect data
Discover all the ways hackers can exploit system weaknesses to steal and corrupt data – and the ways to fight back – with a Master of Science in Information Systems (MSIS), Computer Security Management from Strayer. You’ll learn to design better firewalls and network security systems and how to identify system vulnerabilities, shutting down pathways cybercriminals can use to gain access to networks and private information.
Skills you’ll learn with a Strayer MSIS, Computer Security Management concentration
A Strayer degree can help prepare you for career opportunities in computer security management while offering support, flexible learning options and career planning every step of the way.
- Understand and apply the control objectives for information and related technology framework to perform IT audits.
- Describe information technology general controls based on the Information Technology Infrastructure Library best practices.
- Identify the computer investigation process.
- Compare the various types of cybersecurity tools.
- Demonstrate the ability to develop procedural techniques in crime and incident scenes.
Earn your degree from an accredited university
Strayer University is an accredited institution and a member of the Middle States Commission on Higher Education (MSCHE or the Commission) www.msche.org. Strayer University’s accreditation status is Accreditation Reaffirmed. The Commission’s most recent action on the institution’s accreditation status on June 22, 2017 was to reaffirm accreditation. MSCHE is recognized by the U.S. Secretary of Education to conduct accreditation and pre-accreditation (candidate status) activities for institutions of higher education including distance, correspondence education, and direct assessment programs offered at those institutions. The Commission’s geographic area of accrediting activities is throughout the United States.

Master of Science in Information Systems (MSIS) in Computer Security Management cost breakdown
- 12 courses, $2540 per course
- $65 technology fee each term
- $150 one-time degree conferral fee
- $100 resource kit per course
Estimate the cost of your degree
How much does a Master of Science in Information Systems (MSIS) in Computer Security Management cost?
Estimate the cost of your degree
How much does a Master of Science in Information Systems (MSIS) in Computer Security Management cost?
Expected Graduation
...
Approximate Total
...
*Student is required to take two courses per quarter during disbursement period
PREPARING YOUR RESULTS
Time commitment
Calculate the approximate time commitment of your degree.
| Course load | ... courses/term |
| Classroom time | ... hours/week |
| Terms per year | ... terms |
| Terms to graduation | ... terms |
Cost analysis
Calculate the approximate cost of your degree
| Tuition | ... |
| Books | ... |
| Fees | ... |
| No-cost gen ed | $0 |
| Transfer credits | ... |
| Transfer Credit Scholarship | $0 |
| $4K scholarship | $0 |
| Strayer Learn and Earn Scholarship | $0 |
| Approximate total | ... |
Ways to reduce tuition
$4K Alumni Master’s Scholarship
If you’re a Strayer University Alumni and ready to pursue a master’s degree, our Alumni Scholarship can save you $4,000. All you need to do is register for an eligible Strayer graduate program, maintain a GPA of 2.5 or greater and meet eligibility requirements.
50% off Master’s Scholarship
Enroll in two master’s courses, get 50% off tuition.
*Eligibility rules, restrictions and exclusions apply.
Civic and Community Alliance Scholarship
Ready to earn an affordable Strayer degree? Admitted Strayer or JWMI students who are employed in certain civic roles or volunteer for a nonprofit may be eligible to receive 25% off tuition for the duration of their program.
Explore courses in Strayer’s Master of Science in Information Systems, Computer Security Management
Leverage the power of AI to help optimize operations, drive innovation and create new opportunities for your organization. In this concentration, you’ll gain a comprehensive understanding of AI technologies and the management principles required to drive AI initiatives. You’ll learn how to develop AI strategies aligned with business goals, create implementation roadmaps and overcome common challenges associated with the adoption of artificial intelligence.
Computer Security Management Concentration Courses
Complete your degree from where you live, on your time, in a flexible, 100% online program. Using our online portal, you’ll be able to:
- Access lectures and coursework
- Complete assignments and exams
- Communicate with professors and classmates
- Access student resources and support
From day one, you’ll have a team of advisors and coaches to help you balance college, work and your personal life. Tap into support resources online or at a campus near you.
You’ll have access to:
- Admissions and enrollment support
- One-on-one academic coaches
- Financial guidance and potential cost savings
- Career planning services
The faculty at Strayer University bring years of real-world industry experience to the classroom, offering valuable insight and practical knowledge. They are committed to supporting your professional goals and are responsive to questions and concerns through the virtual courseroom.
What can you do with an MSIS, Computer Security Management degree?
Your education can help you pursue your professional and personal goals. While Strayer cannot guarantee that a graduate will secure any specific career outcome, such as a job title, promotion or salary increase, we encourage you to explore the potential impact you can have in the information systems field.
Versatile skills for your future
The computer security management concentration can provide the skills to help you safeguard computer network systems against malware, intruders and other threats.
In addition, students who complete this concentration will be prepared to:
- Verify the functionality of data processing activities and security measures by conducting risk assessments and tests on data processing systems.
- Create documentation for computer security and emergency measures policies, procedures and tests.
- Manage data file use and control access to computer files to protect information.
- Conduct analyses of web service network traffic or waveforms to identify anomalies.
- Develop computer information resources, support data security, strategic computing and disaster recovery.
- Meet with users, management, vendors and technicians to evaluate computing needs and system requirements.
- Review an organization’s technology use and suggest enhancements, including hardware and software upgrades.
- Determine project feasibility and requirements based on data processing proposals.
86
of Strayer master's alumni agree that Strayer was the right choice for earning their degree.
Strayer Alumni Survey, 2023
Apply for your Computer Security Management degree today
An admissions officer can help you choose the right program, register for classes, transfer credits and find cost-savings opportunities.
Here’s what you’ll need to get started:
Spring classes start on April 6
Learn more about Strayer University’s admissions process.
Transferring to Strayer from another university?
Transfer up to four eligible classes from a prior college or university to your master’s degree, saving time and money.
Strayer welcomes international students
Strayer University is proud to have hosted more than 4,000 international students from over 143 countries. Earn your degree in the U.S. or completely online in your home country – it’s your choice.

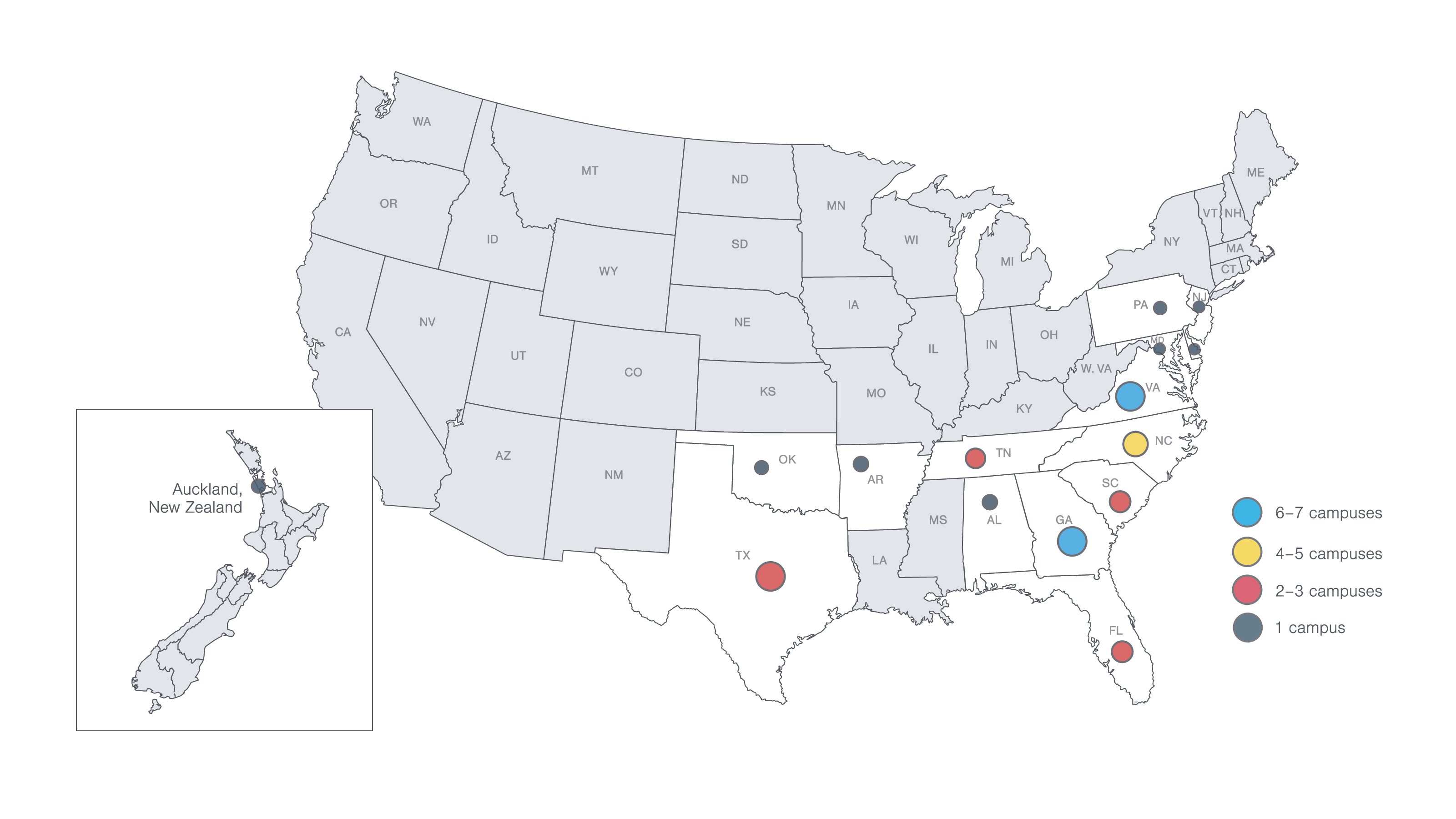
Campus locations
Come to a campus near you for guidance and support. You’ll have access to helpful resources, a supportive community and plenty of spaces to learn and grow.
Ready to take the next step?
Your admissions officer is here to guide you through every step of the process, from completing your application to choosing your concentration.